ASSESSMENT AND RESPONSE
ASSESSMENT
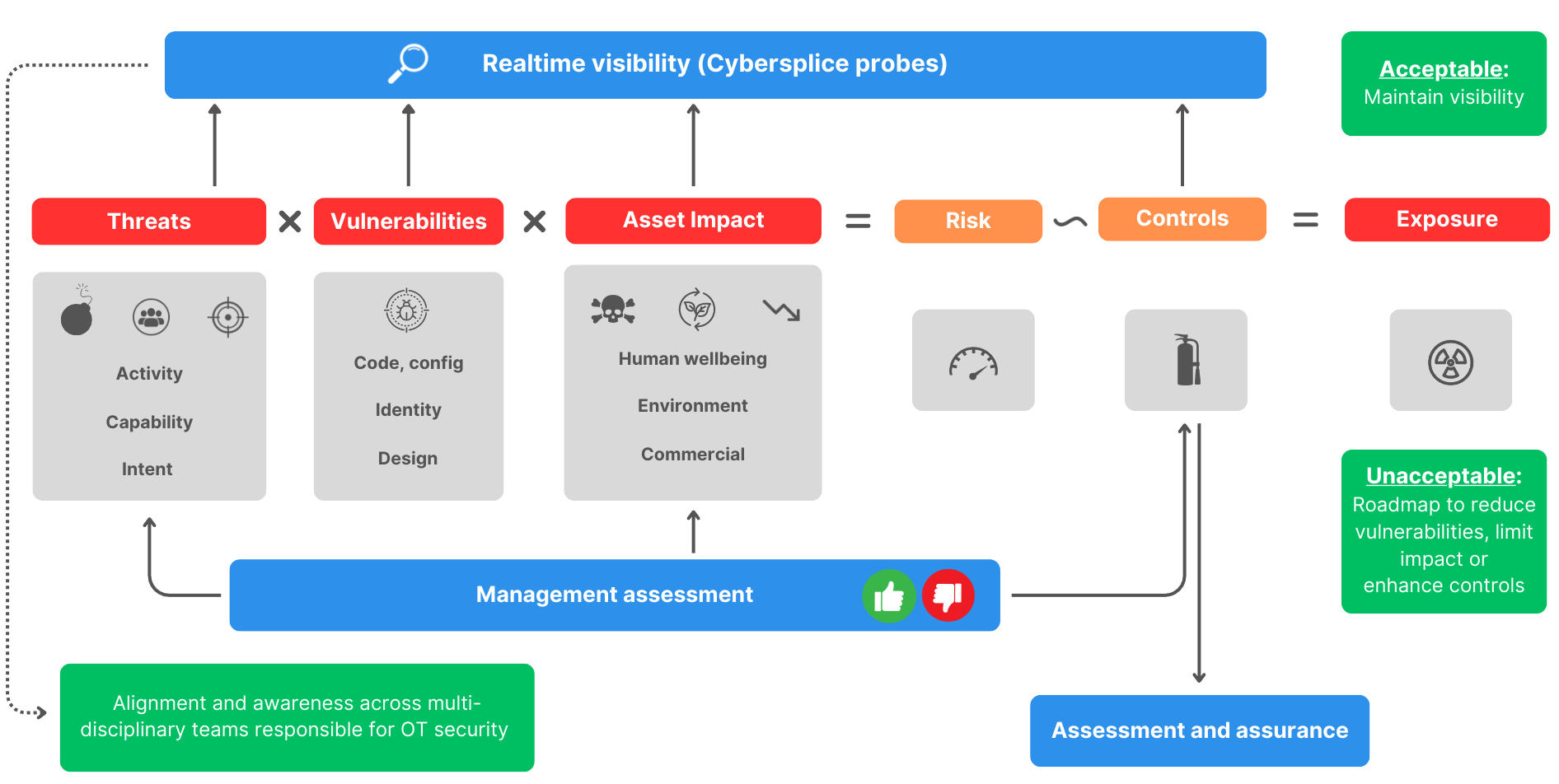
There are two prerequisites to effectively manage cyber-physical exposure: awareness and visibility
Awareness requires understanding threat capability and intent, vulnerabilities, the potential impact on assets, environment and human well-being, as well as the options available to manage risk (i.e. to reduce the likelihood of these elements connecting or to reduce the potential resulting impact).
Although visibility is required across the elements mentioned above, visibility into vulnerabilities as well as whether these vulnerabilities are actively being targeted is key to detecting and responding to attacks, in order to minimise potential damage from a security compromise. Visibility could mean the difference between an incident with a minor impact and a catastrophe.
Cybersplice provides professional assessment services to assist our clients to understand cyber-physical exposure. We provide risk and threat assessments, control capability maturity assessments, and assessments against industry standards. We bring visibility to assets and asset behaviours on the OT network using Splice. These elements are matched to understand exposure and prioritise actions into a tailored roadmap.
Cybersplice’s methodology to measure Cyber-physical Exposure and improve Cyber-physical Resilience is depicted in the diagram below:
CYBER-PHYSICAL EXPOSURE ASSESSMENT
To facilitate the visibility required during Cyber-physical exposure assessments, Splice zero-touch or rapid deployment options are leveraged.
INCIDENT RESPONSE
When dealing with a cyber-physical attack, time is of the essence. Unless organisations planned for and test response capabilities up front, the situation may be overwhelming. Cybersplice guides customers through the response process and assists with understanding the depth of compromise, appropriate action to reduce the potential impact, and eradication options to restore Operations to a known state.
Get in touch via the IM link or contact form for assistance.
In addition to on-demand Incident Response assistance, Cybersplice also facilitates developing and exercising the Incident Response capability through tabletop and hybrid simulations.